Security experts have raised concerns over the vulnerability of the widely-used ‘Advanced Custom Fields’ and ‘Advanced Custom Fields Pro’ plugins for WordPress, which could be exploited by attackers for cross-site scripting (XSS) attacks. These plugins are popular for custom field building and have been installed on millions of websites globally. The vulnerability, which was discovered by Patchstack’s researcher Rafie Muhammad on May 2, 2023, has been assigned the CVE-2023-30777 identifier and is considered a high-severity reflected XSS vulnerability. Although the vulnerability requires an attacker to have access to the plugin, it could still enable them to steal confidential information or gain additional privileges on a targeted WordPress site. While the plugin’s developer has released a security update in version 6.1.6 to address the issue, users are advised to update their plugins as soon as possible.
The XSS flaw
The CVE-2023-30777 flaw stems from the ‘admin_body_class’ function handler, which failed to properly sanitize the output value of a hook that controls and filters the CSS classes (design and layout) for the main body tag in the admin area of WordPress sites.
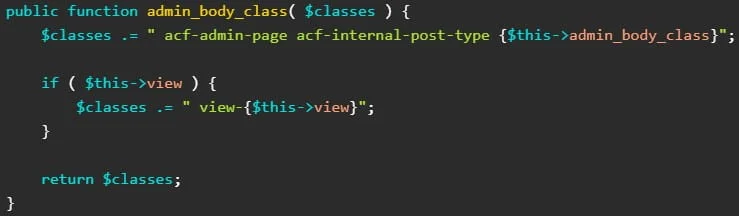
An attacker can leverage an unsafe direct code concatenation on the plugin’s code, specifically the ‘$this→view’ variable, to add harmful code (DOM XSS payloads) in its components that will pass to the final product, a class string.
An attacker can leverage an unsafe direct code concatenation on the plugin’s code, specifically the ‘$this→view’ variable, to add harmful code (DOM XSS payloads) in its components that will pass to the final product, a class string.
The vulnerability in the plugin was addressed by the developer through the implementation of a new function called ‘esc_attr’ in version 6.1.6. This function effectively sanitizes the output value of the admin_body_class hook, preventing any possibility of XSS attacks. Therefore, users of ‘Advanced Custom Fields’ and ‘Advanced Custom Fields Pro’ are strongly advised to update their plugin to version 6.1.6 or later as soon as possible to avoid any potential security breaches. According to WordPress.org download statistics, over 72% of users are still running versions prior to 6.1, which are susceptible to XSS and other known vulnerabilities.